
How to Protect Yourself Against Social Engineering
In an era where our digital lives are intricately interwoven, protection against social engineering has become paramount. This deceptive strategy preys on human psychology, making awareness and caution the strongest shields. Here’s a concise guide on safeguarding yourself against social engineering.
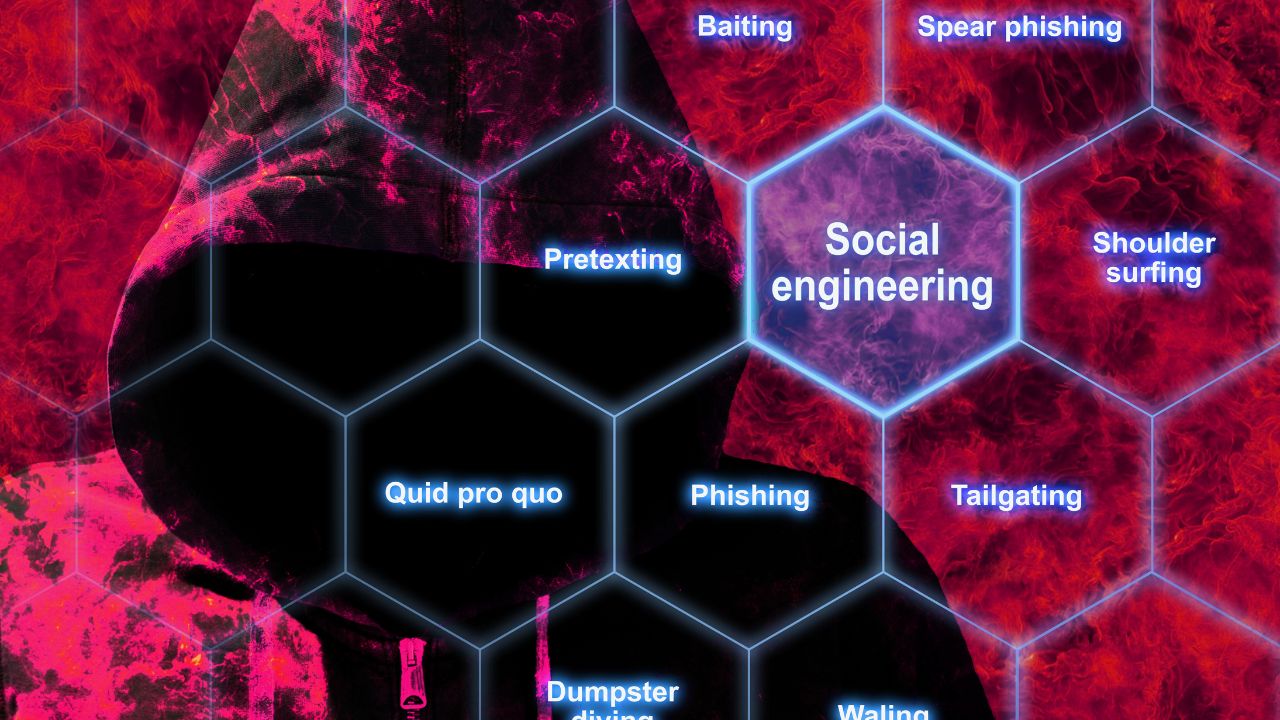
1. Educate Yourself: Understanding social engineering tactics is the first line of defense. Learn about phishing, pretexting, baiting, and impersonation. Familiarize yourself with common red flags, such as urgent requests for sensitive information or unsolicited emails.
2. Verify Requests: Always verify the authenticity of requests, especially those asking for personal or financial information. Contact the person or organization through official channels before sharing any sensitive data.
3. Strengthen Passwords: Use strong, unique passwords for each account. Combine letters, numbers, and symbols, and avoid easily guessable information like birthdays. Consider a reputable password manager for added security.
4. Two-Factor Authentication (2FA): Enable 2FA wherever possible. This adds an extra layer of security, requiring not only a password but also a secondary verification method, such as a code sent to your phone.
5. Privacy Settings: Adjust privacy settings on social media platforms. Limit the information visible to the public and avoid sharing personal details that could be exploited.
6. Be Skeptical: If something seems too good to be true or creates a sense of urgency, be skeptical. Social engineers often play on emotions to manipulate responses.
7. Email Caution: Don’t click on links or download attachments from unfamiliar or suspicious sources. Hover over links to see their actual URLs before clicking.
8. Employee Training: Organizations should conduct regular employee training to raise awareness about social engineering. This can reduce the risk of breaches stemming from within the organization.
9. Physical Security: Social engineering isn’t limited to the digital realm. Be cautious of tailgating attempts, where unauthorized individuals gain entry by following someone with access.
10. Report Suspicious Activity: If you suspect a social engineering attempt, report it to the appropriate channels. This can help prevent others from falling victim.
In the ever-evolving landscape of cybersecurity, knowledge and vigilance are your best tools. By staying informed and adopting cautious practices, you can effectively shield yourself from the manipulative tactics of social engineers. Remember, an ounce of prevention is worth a pound of cure in the digital world.
