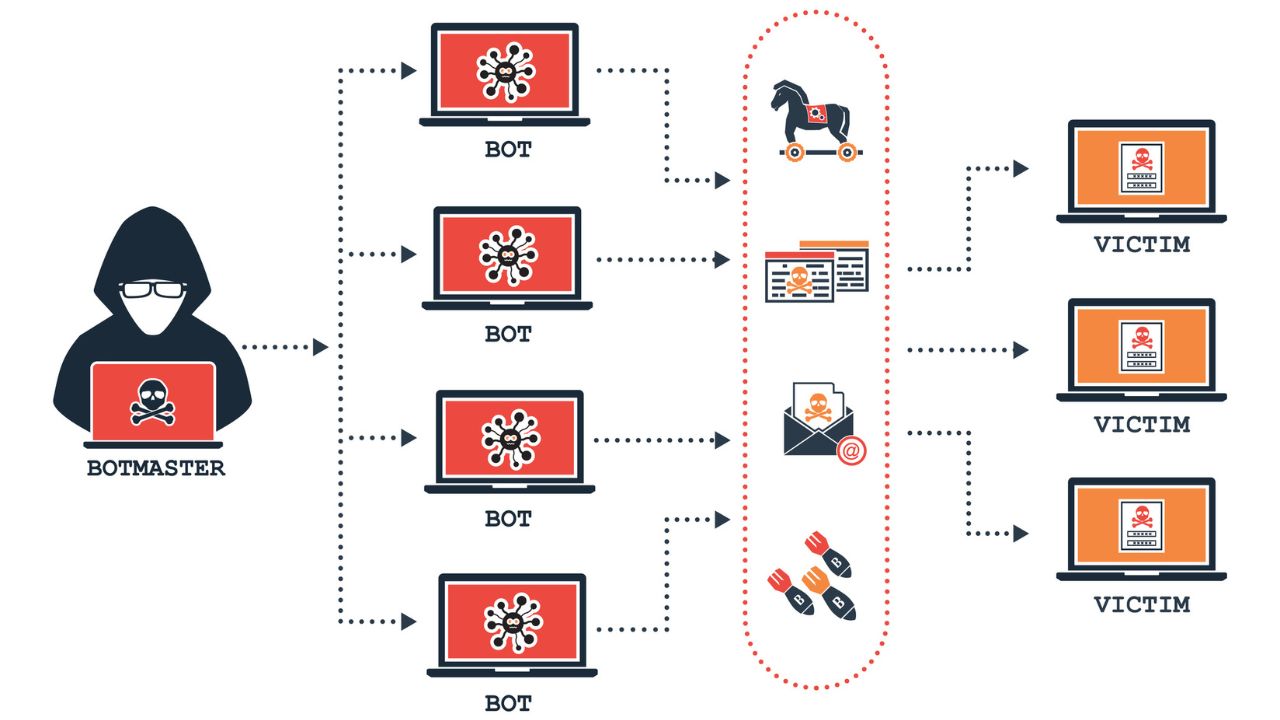
What is a BotNet and how does it work?
A botnet is a network of compromised computers, often referred to as “bots” or “zombies”.

They are remotely controlled by a malicious actor, known as the “botmaster” or “bot herder.”
These compromised computers are typically infected with malicious software, often called “malware“, which allows the attacker to control them without the knowledge or consent of their owners.
Here are key characteristics and information about botnets:
-
Infection and Control:
- Botnets are created by infecting a large number of computers with malware, which can be distributed through various means such as email attachments, malicious websites, or software vulnerabilities.
- Once a computer is infected, it becomes part of the botnet and can be remotely controlled by the botmaster.
-
Command and Control (C&C):
- Botnets are centrally controlled through a Command and Control server (C&C server), which is operated by the attacker. The C&C server issues commands to the infected computers, coordinating their actions.
- The communication between the infected computers and the C&C server is often designed to be covert to avoid detection.
-
Malicious Activities:
- Botnets are commonly used for carrying out various malicious activities, such as distributed denial-of-service (DDoS) attacks, spamming, click fraud, information theft, and spreading other malware.
- DDoS attacks involve overwhelming a target’s servers or network infrastructure with a flood of traffic from the infected computers, causing service disruption.
-
Persistence and Resilience:
- Botnets are designed to be persistent, with the ability to survive system reboots and attempts at removal. They may employ techniques to hide their presence and resist detection by security software.
- Some botnets are decentralized, using peer-to-peer communication between infected computers rather than relying on a central C&C server. This makes them more resilient to takedown efforts.
-
Evolution and Sophistication:
- Botnets continue to evolve in terms of sophistication and capabilities. Some employ advanced evasion techniques to bypass security measures, and others use encryption to secure communication between infected computers and the C&C server.
- As security measures improve, botnets may adopt new tactics to avoid detection and removal.
-
Legal Consequences:
- Operating or participating in a botnet is illegal in many jurisdictions. Authorities and cybersecurity organizations work to identify and dismantle botnets, and individuals involved in their creation or operation may face legal consequences.
Protecting against botnets involves maintaining up-to-date security software, regularly updating operating systems and applications, using strong and unique passwords, and being cautious about downloading attachments or clicking on links in emails or websites. Additionally, network administrators can implement measures to detect and mitigate botnet activity within their networks.
